As internet services get more intermixed - with new technologies building off older ones - a weak link in the chain can create issues for everyone. For example, if your developers are some of the reasonable millions who used the Log4j framework in your application, that may have left your company vulnerable to exploitation by hackers installing malware or the intelligence agencies of a foreign government. While this example is extreme, the nature of software is such that your developers rely on 3rd party tools to build what you’re asking them to build, and each one is a risk to your operations.
In order to go fast and not break things, well-timed and frequent vulnerability scans let you discover and remediate issues anywhere in your tech stack as quickly as possible. These scans look through the hundreds of packages and libraries embedded in your ML models and flag vulnerabilities for your team to remediate.
Standard operating procedure is to run through a rigorous vulnerability scan before these ML models are deployed. It’s normal for an enterprise to establish governance to block releases when a security vulnerability is discovered - some even require zero vulnerabilities before release.
But vulnerability scanning only works when you remember to do it - and it has become another to-do item on the seemingly ever-growing list of operational complexities for machine learning. Existing checkpoints and tools available to the rest of the software stack might not work on ML Models and their intricacies.
At Verta, we’re proud to offer vulnerability scanning at multiple-points of the ML lifecycle to help your models get to production faster and stay secure when they’re deployed.
How does it work?
1. As part of your Verta implementation process, you will configure the image scanning software you use so it’s there for your team when they need it. As a default, we’ll connect Amazon ECR and Amazon Inspector so you’re covered even if you don’t customize it. You’ll set this up once and leverage it for every model deployed.
2. At various points in the model lifecycle, Verta will run a vulnerability scan automatically (or you can kick it off the with the click of a button), for example:
- When you register a release ready model in Verta Model Catalog
- When you go to download model images
- Before you deploy a model
- When monitoring a live endpoint
3. In a few seconds the scan will be complete. Verta will show you a report of:
- The number of Critical, High, Medium and Low risk vulnerabilities detected (hopefully zero!)
- What packages the vulnerabilities were found in and a brief description of each issue
Vulnerability Scanning Report Example
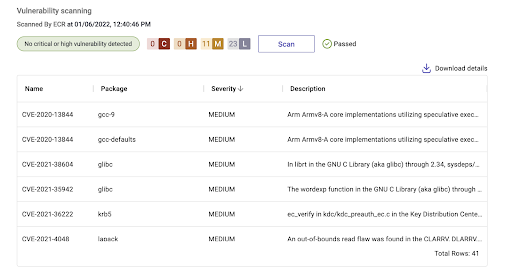
Of course, you can configure governance in the Verta platform to prevent deployments before a scan is conducted or if a threshold of vulnerabilities is detected. You can also leave it up to the judgment of your team based on the location and severity of the vulnerabilities.
As the model is in “operate” mode and you are monitoring, we continue to offer vulnerability scanning as your model is operating because new defects, configurations, environmental changes or unexpected interactions are constantly occurring.
With this toolkit we aim to make discovering and analyzing vulnerabilities easy, leaving you with more time to coordinate a response and react to the vulnerability, giving peace of mind when there are no issues found.
If you’d like to see first-hand how the magic happens, connect with us for a demo.
Subscribe To Our Blog
Get the latest from Verta delivered directly to you email.

.png)